This week, I took the Certified Ethical Hacker exam – again… The first attempt at the exam didn’t make for a happy story. I was convinced that they couldn’t possibly have lost all of my work – the database must have stored each answer as I submitted it, surely?!
I went backwards and forwards with EC-Council to no avail. They offered an “upgrade” to an exam held at a test centre but that was a step backwards as far as I was concerned. Having assured me that they’d resolved the issue with the web app, I rescheduled the online exam. I’ll come back to the exam process later but I want to talk about certifications in general, why I was looking at CEH certification and how I prepared for it.

Certifications
I’ve been working in software development for a long time and I’ve never felt a definite need for certification. I’ve done a lot of recruitment over the years, I’ve looked at a lot of software developer CVs and certifications have always been a bonus feature and never a requirement.
Impostor syndrome seems to be very common amongst software developers and I count myself in that group. I have, from time to time, wondered if a certification would validate that I can actually develop software against a recognised standard, say Microsoft Certified Solution Developer.
Looking at the certifications available though, I’ve never been content that they were validating the right thing so I’ve focused on learning and continuous development, comparing notes with peers in the industry to benchmark myself.
So why did I even get into this process at all?
Why I started on the path to CEH
I’ve been into security for years – it was probably down to WarGames. The school computer lab was the location of a wargame of a different type where we’d pwn each other’s accounts, or the teacher’s. This was a more innocent time – a long time before the UK Computer Misuse Act!
Information security is intertwined with software development. The internet makes the software that we write accessible to users good and bad, and I’ve always been very conscious of that. One of the earliest bits of professional software that I wrote would hash the contents of a website so that unauthorised modifications could be detected.
Security doesn’t get enough attention from software developers though so I’ve been speaking on the subject for a couple of years to developer user groups. I gave a lightning talk on OWASP ZAP at .NET Oxford recently. Here’s a talk I did to London .NET at Skills Matter last year.
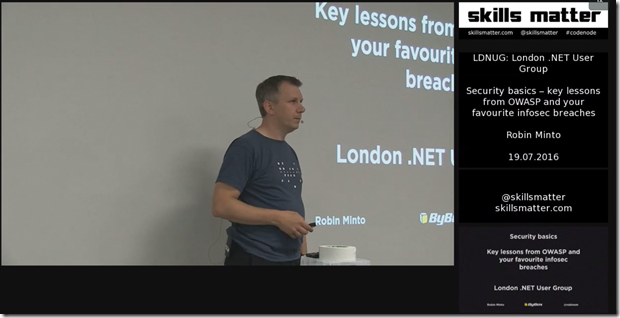
I’ve spoken at DDD Reading, DDD South West and I’m speaking about authentication at DDD East Anglia next month.
I’ve been to many events and user groups as an attendee and it’s fantastic to give something back as a speaker. I’ve been incredibly lucky to be chosen to speak at all of these events but I’d like to do more. Along the way though, I’ve felt that imposter syndrome creeping back in – why should these people spend their incredibly valuable time listening to me?
My job title has never been Security Consultant, Pen Tester or CISO but I’ve got the knowledge to share. Wouldn’t it be useful if I had a certificate to prove it!
Selecting the Certified Ethical Hacker certification was straightforward. I was familiar with that cert and the competing qualifications. CEH is broadly recognised, even approved for meeting US Department of Defense job requirements.
All I needed to do was pass the exam.
Preparation
With the knowledge in hand, I wondered if I really needed to spend £4,000 for an intensive 12 hour a day, 5-day course to get a certification. Sitting the exam, without the training, is just $750 US.
It would have been unwise to sit the exam with no preparation even with a broad knowledge of infosec. I needed to make sure I’d covered the syllabus. The key, for me, came from Pluralsight. They have a wide range of video-based training material and a CEH track from Troy Hunt and Dale Meredith.
I’ve followed Troy Hunt’s blog for years. I’ve been to his Hack Yourself First workshop. He’s a great public speaker. I didn’t know much about Dale Meredith but I do know the efforts that Pluralsight and their authors go to in producing content so I was happy he’d be able to deliver.
I work at ByBox and we encourage the team to use Pluralsight as part of their training. This means the Pluralsight subscription was ready to go.
There’s a further reason why video-based training was a good way to go for me and it’s an interesting one… cycling. Last year, I invested in a smart-trainer that turns a road bike into an interactive cycling game via Zwift. The photo below shows a similar setup to mine. This was great for improving my fitness over the winter but I found I could train and watch Pluralsight videos at the same time. Two types of training combined!

Handily, a Humble Bundle of security eBooks containing Certified Ethical Hacker Version 9 Study Guide came up so I added that to the training (but not on the bike). I knew some memorisation of tools and processes would be required. For example, I don’t spend every day using nmap and you’re expected to know all of the command line options.
At somewhere between 1.5x and 2x speed, I got through the 76 hour Pluralsight CEH track in around 40 hours. I had probably spent another 5 hours on extra learning. Was I ready?
The Exam
As I mentioned, my first attempt at the CEH exam didn’t go well. As I started the four-hour exam at the second attempt, I did a bit of QA testing of my own. I talked about the mechanics of the exam process in that blog so I won’t go into them here but having moved on to the second question, I went back to review the first, knowing that had caused an error last time round. Everything seemed to be working properly – perhaps I’d get through this thing?
You’re allowed nearly two minutes per question and I found that was plenty. To make sure I didn’t run out of time inadvertently, I’d mark questions for review where I wasn’t comfortable with the answer so I could return to them later. I spent about an hour and a half answering all the questions and an extra 15 minutes going over questions that needed extra attention.
I probably spent some extra time trying to interpret the questions and answers. It was clear that they’re not all from the same author – some aren’t from native English speakers:
Secure Sockets Layer (SSL) use the asymmetric encryption both (public/private key pair) to deliver the shared session key and to achieve a communication way
I have a lot of respect for those writing in a second language. The English language is fluid and we’re not computers so we can interpret meaning but I think clarity of questions would benefit everyone.
Infosec is a broad subject and the CEH syllabus is sufficiently broad to match. It goes into enough depth so that you have a good understanding of the topics but there’s always room to go deeper. Armed with this level of knowledge, it’s easier to find out more. I’m not likely to spend much time in buffer overflows but if I need to, I have a good start.
The Result
I did wonder how quickly I’d get results from the online exam. Would the answers have to go for some sort of verification? I was very thankful that the result came immediately – I’d passed.

Taking the exam twice was not what I had planned and I’m relieved that the process is now complete. I do believe that “every day’s a school day” and I’ve certainly learnt through training for the CEH certification. I won’t be standing up at speaking events with my certificate in hand but I will add it to the bio and hopefully people will feel it’s worth seeing me speak. See you at the next one?
Monday was an interesting day; I sat the Certified Ethical Hacker exam with the intention of receiving certification from EC Council. I'll leave my reasons for taking the exam for another post - hopefully one saying that I've passed…

It's been years since I last sat an exam. Back then, I would have been sat in an exam hall with pen and paper. But things have changed and exams can be taken online – remotely monitored with a proctor watching via webcam and screen-sharing. Great – I don’t even need to leave the house!
To take the exam, you start a webcam and chat session with a proctor at a company like ProctorU. They check your ID and you point your webcam around your workspace and around the room so they can see that you don’t have smartphones or any other way of cheating. It struck me that all those taking this “hacker” exam would be thinking about all the ways they could beat this system, if it weren’t for the “ethical” bit.
The proctor then takes you to the exam website where you log in, prove that you’ve paid with a one-time voucher code and select the exam that you’re taking. The proctor logs in and you accept various conditions (no break for four hours!) and you’re ready to start. I won’t dwell on the fact that the proctor is using credentials that are clearly common to everyone at the company – it’s not the first time I’ve seen that. As with all hackers, this one is wearing a hoodie but this is an ethical hacker so it’s beige.
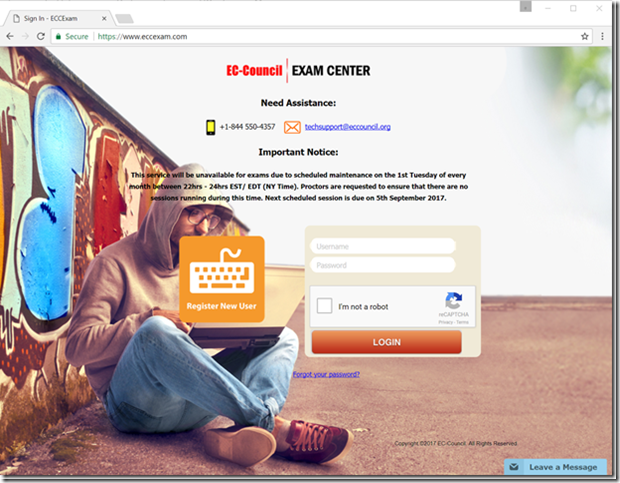
I went through this process and began my exam. There are 125 multiple choice questions to answer – select a radio button and click the Answer button and the website progresses to the next question. I’m assuming that this is a PHP web app by the file extension in the URL. It’s straightforward stuff – the browser submits the form and the website returns the next page of question and answers. There’s also a checkbox to mark a question for review and a drop down list containing all the questions that have been answered with a Review button next to it.
I’m about 18 questions in and I think I’ve been a bit hasty on the previous question. I select it from the list and hit Review. That’s when I hit the first problem.
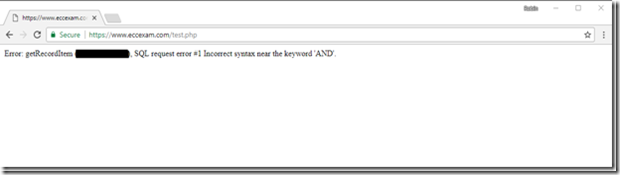
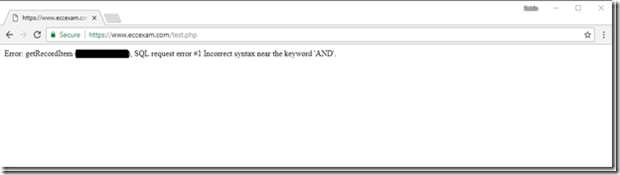
Ok, so I get a page with an error message with SQL syntax error. I’ve redacted what would seem to be a database table name in the error message – I don’t want to be the one sharing their database schema around the web.
Error: getRecordItem (<TABLE NAME HERE>), SQL request error #1 Incorrect syntax near the keyword 'AND'.
Improper Error Handling is covered in the OWASP Top 10 under Security Misconfiguration but I don’t have time to worry about that during my exam. I get in touch with the proctor to see if they can help. They try refreshing the page and opening new browser windows and going back through the exam selection process but it’s no good – the error message seems to be here to stay. They escalate to a colleague who tries the same things with no success. My exam voucher code is single use so I can’t even restart the exam.
At this point, the proctor says “We’ve sent an email to our contacts and they should contact you within three to six days” and I’m shocked. I can’t compare the stress levels now to those I had during university exams but the adrenaline is flowing. I’ve got a busy work calendar at the moment and rescheduling isn’t going to be easy. I’ve got a conference call following the exam. I go and get my mobile phone (having asked permission!) and call the EC Council helpline.
I get various ring tones as the call is bounced around the world. There’s a delay of a few seconds and communicating is a challenge. A few emails and phone calls and some time later and my one-time voucher code has been reset and I can restart the exam.
At this point, it’s an hour and a half after I first started and I restart the exam. I need to take more care as I answer the questions this time as I’m not going to risk trying to review questions later for fear of the same problem re-occurring.
I make good progress and I have time to spare as I reach the end of the questions. I select the last answer option and hit the Answer button on question 125.
Oh wow. My head is now in my hands as I start to think about what’s just happened. That error message again.
I contact the proctor. I’ve been handed over to a new person so I have to explain the situation again. Browser is refreshed. New tabs are opened. Error remains.
I fire off an email to EC Council technical support. The error message basically tells me that the answers are stored in a database so they should be able to retrieve them so I don’t have to re-sit the exam, right?
Apologies for the inconvenience caused.
We have reset your voucher code. Please reschedule the exam date for tomorrow.
We appreciate your patience and understanding of this matter.
I reply. Are they telling me that the answers aren’t stored in the database?
We apologize for the inconvenience caused, we regret to inform you that as the exam was not submitted successfully due to the technical difficulties we do not have logs from your exam to issue you with your certification.
We are happy to help you with the exam voucher of your choice valid for a period of 1 year and you can proceed to reschedule your exam with it.
Have a nice day!
I’ve replied again and I’m waiting for a response. Did the application really fail to store any of my answers to the database? Why would I repeat any exam that’s so likely to lose my data and waste my time? If ProctorU recorded my screen for the duration of the exam, can we rebuild the data?
For the answers to these questions and more, watch this space!
There’s a new HTTP header on the block - HTTP Public Key Pinning (HPKP). It allows the server to publish a security policy in the same vein as HTTP Strict Transport Security and Content Security Policy.
The RFC was published last month so browser support is limited, supported in Chrome 38, Firefox 35 and newer. However, there are helpful articles from Scott Helme, Tim Taubert and Robert Love on the topic and OWASP has some general info on certificate and key pinning in general. Scott has even built support for HPKP reporting into his helpful reporting service - https://report-uri.io/.
Although Chrome and Firefox will honour your public key pins, testing the header is slightly tricky as they haven't implemented reporting yet (as of Chrome 42 and Firefox 38). I spent some time trying to coax both into reporting, working under the assumption that they must have implemented the whole spec right? It seems not.
In writing this, I also wanted to note the command I used to calculate the certifcate digest that's used in the header. In contrast to other examples, this connects to a remote host to get the certificate (including allowing for SNI), outputs to a file and exits openssl when complete.
echo |
openssl s_client -connect robinminto.com:443 -servername robinminto.com |
openssl x509 -pubkey -noout | openssl pkey -pubin -outform der |
openssl dgst -sha256 -binary | base64 > certdigest.txt
I won't be using HPKP in my day job until reporting support is available and I can validate that the configuration won't break clients. There's great potential here though once the support is available.
I’ve been using the ASafaWeb security analyser to scan various websites that I work on. It picks up basic configuration problems in .NET websites and, very handily, will scan periodically to make sure that misconfiguration doesn’t creep back in.
ASafaWeb was created by Troy Hunt, a software architect and Microsoft MVP for Developer Security based in Australia. Troy writes some great articles on improving application security, with a focus on .NET, and he links to those articles in ASafaWeb to illustrate why and how improvements should and can be made.
Most of the issues can be addressed in the application, generally in web.config, but the issue I’m interested in here can be solved by configuring at the server level. Here’s the output from ASafaWeb:
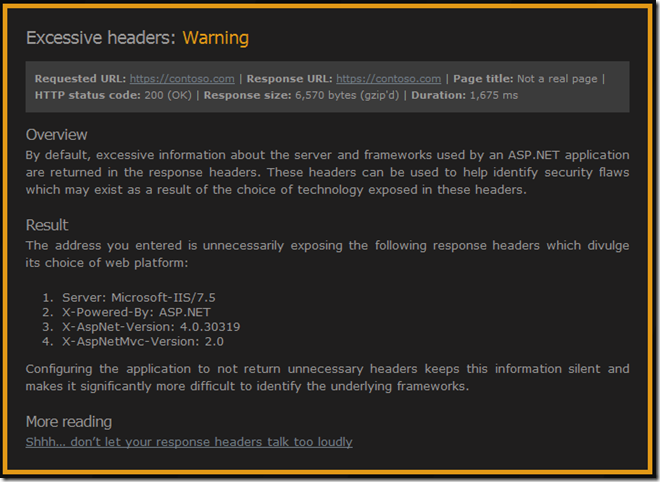
See that “X-Powered-By: ASP.NET” header? That one’s inherited from the IIS root configuration. We could remove it in every web.config but better to remove it once.
Troy links to his blog post on removing all of those headers – Shhh… don’t let your response headers talk too loudly. As he mentions, there are many different ways of removing those headers – he goes into IIS Manager UI and removes it from there.
I’m trying to make sure that I script server configuration changes. This is a great way of documenting changes and allows new servers to be configured simply. I want servers that can rise like a phoenix from the metaphorical ashes of a new virtual machine rather than having fragile snowflake that is impossible to reproduce (thanks to Martin Fowler and his ThoughtWorks colleagues for the imagery).
So, the script to remove the “X-Powered-By” header turns out to be very straightforward once you figure out the correct incantations. This assumes you have Powershell and the Web Server (IIS) Administration Cmdlets installed.
Import-Module WebAdministration
Clear-WebConfiguration "/system.webServer/httpProtocol/customHeaders/add[@name='X-Powered-By']"
That’s a lot of words for a very little configuration change but I wanted to talk about ASafaWeb and those ThoughtWorks concepts of server configuration. I also need to mention my mate Dylan Beattie who helped me out without knowing it. How? StackOverflow of course.